CSD’s macOS security configuration team is working to develop secure system configuration baselines supporting different operational environments for Apple macOS version 10.12, “Sierra.” These configuration guidelines will assist organizations with hardening macOS technologies and provide a basis for unified controls and settings for federal macOS workstation and mobile system security configurations. The configurations are based on a collection of resources, including the existing NIST macOS configuration guidance, the Defense Information Systems Agency (DISA) macOS Security Technical Implementation Guide (STIG), and the Center for Internet Security (CIS) macOS Security Benchmark.
The project team researched and tested approximately 270 settings for macOS 10.12. The configuration set has been significantly reduced due to changes in the operating system’s features and default setting values. Among other collected data, each setting has a designated Common Configuration Enumeration (CCE) number, which aids in its long-term tracking. Figure 1 illustrates the various categories that comprise the baselines. Note that a higher quantity of settings in a category does not imply greater importance over other categories.
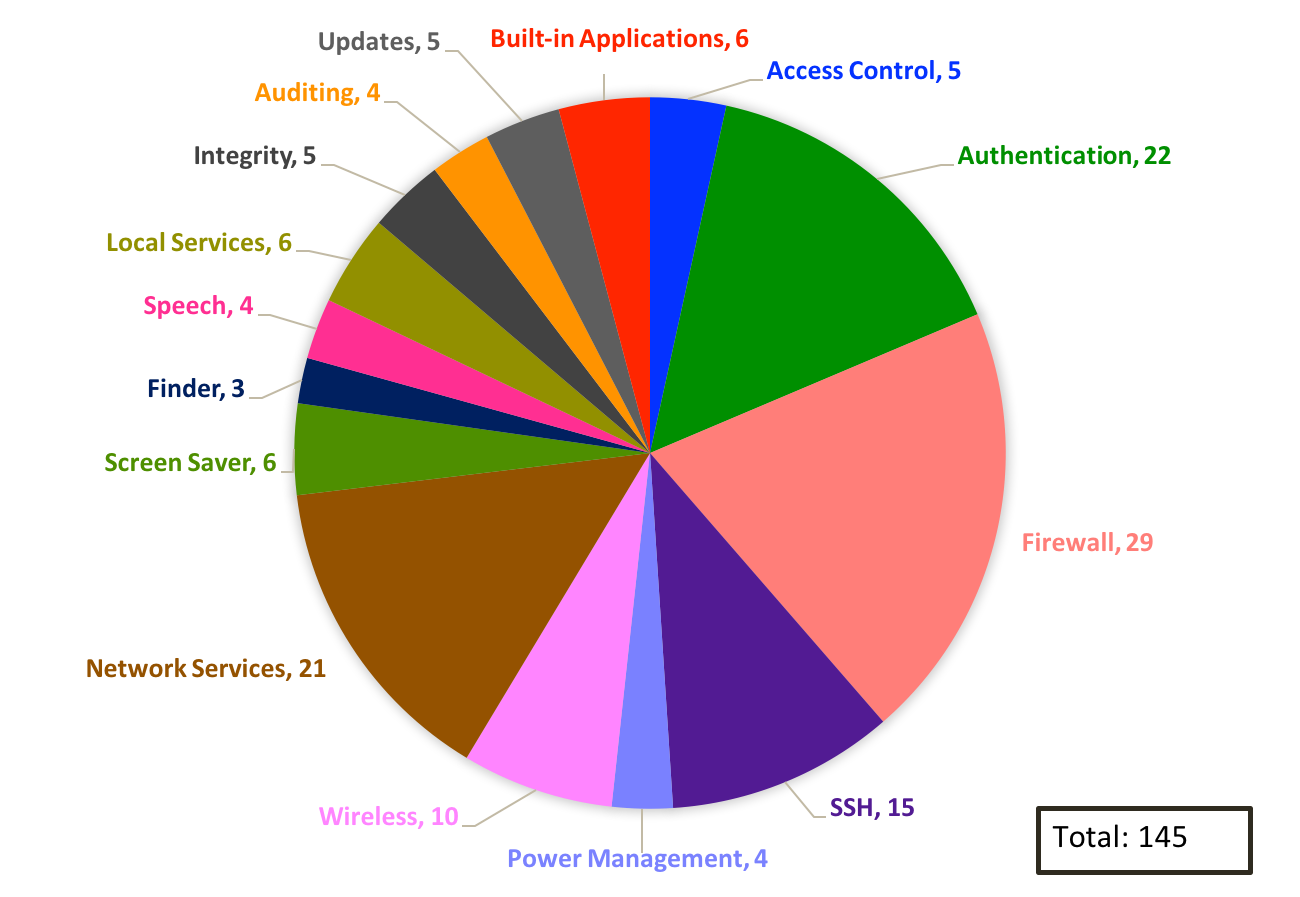
Figure 1: Configuration Categories
The shell scripts that apply the settings to a macOS 10.12 system are organized into three key baselines, which are appropriate for different environments:
- The Standalone baseline describes small, informal computer installations that are used for home or business purposes,
- The Managed baseline is appropriate for centrally managed, networked systems, and
- The Specialized Security-Limited Functionality (SSLF) baseline is appropriate for systems where security requirements are more stringent and where the implementation of security safeguards is likely to reduce functionality.
 An unofficial archive of your favorite United States government website
An unofficial archive of your favorite United States government website


