Ransomware Protection and Response
Overview
Thanks for helping shape our ransomware guidance!
Our new resources on tips and tactics for preparing your organization for ransomware attacks are here!
Ransomware is a type of malicious attack where attackers encrypt an organization’s data and demand payment to restore access.
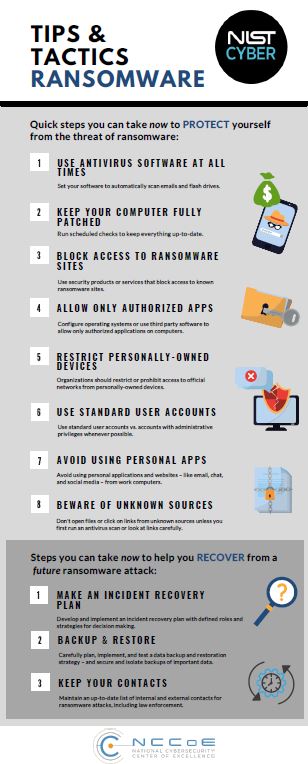
Here’s an example of how a ransomware attack can occur:
- A user is tricked into clicking on a malicious link that downloads a file from an external website.
- The user executes the file, not knowing that the file is ransomware.
- The ransomware takes advantage of vulnerabilities in the user’s computer and other computers to propagate throughout the organization.
- The ransomware simultaneously encrypts files on all the computers, then displays messages on their screens demanding payment in exchange for decrypting the files.
Ransomware disrupts or halts an organization’s operations and poses a dilemma for management: does the organization pay the ransom and hope that the attackers keep their word about restoring access, or does the organization not pay the ransom and restore operations themselves?
Fortunately, organizations can take steps to prepare for ransomware attacks. This includes protecting data and devices from ransomware and being ready to respond to any ransomware attacks that succeed.
Here are NIST resources that can help you with ransomware protection and response.
My organization needs to...
Created May 04, 2021, Updated February 24, 2022
 An unofficial archive of your favorite United States government website
An unofficial archive of your favorite United States government website


