The Cryptographic Algorithm Validation Program (CAVP) and the Cryptographic Module Validation Program (CMVP) were established on July 17, 1995 by NIST to validate cryptographic modules conforming to the Federal Information Processing Standards (FIPS) 140-1, Security Requirements for Cryptographic Modules, and other FIPS cryptography based standards. FIPS 140-2 was released on May 25, 2001 and supersedes FIPS 140-1.
The current implementation of the CMVP is shown in Figure 1 below. The CAVP is a prerequisite for CMVP. The CAVP and CMVP leverage NVLAP-accredited Cryptographic and Security Testing (CST) laboratories for testing cryptographic algorithms with CAVP and validation testing against the Derived Test Requirements (DTR), Implementation Guidance (IG), and applicable CMVP programmatic guidance. According to existing guidance, the CST laboratories must perform 100% independent testing of the modules submitted by the vendors.
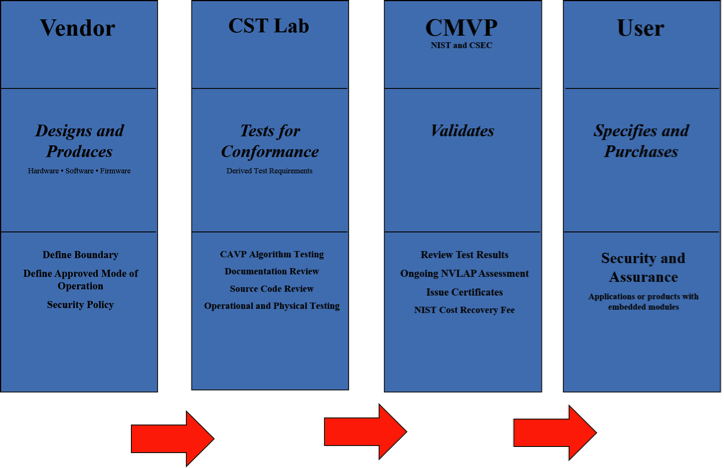
Figure 1: Current implementation of the CMVP
In the flows of the process under which the CMVP operates, shown below, there is no interaction between the CMVP and module vendors. All CMVP communications are with the testing laboratories. 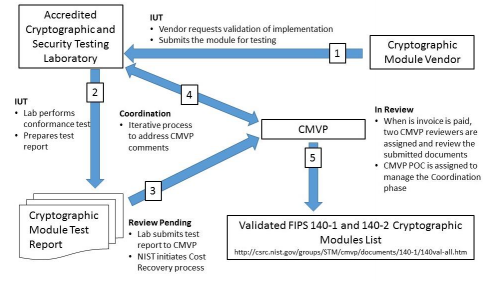
The structure and the rules under which the CAVP and CMVP operate worked well for the level of the technology utilized by the Federal Government at the time when the programs were created more than two decades ago. As technology has advanced however, the algorithm and module testing processes no longer satisfy current day industry and government operational needs. Testing and validation of test results are exceedingly long, well beyond typical product development cycles across a wide range of technologies. Because of the human effort involved in all stages of this process, the possibility for subjectivity and errors is high. Moreover, the resulting validated modules do not provide useful interfaces for integration into IT systems to enable run-time monitoring of modules for compliance with FISMA.
NIST recognizes the need to improve the efficiency and effectiveness of cryptographic module testing in order to reduce the time and cost required for testing while providing a high level of assurance for Federal government consumers.
Purpose
The principal goals of this project are to collaborate with commercial or open source producers of cryptographic capabilities and government consumers of FIPS 140 validated modules in order to:
- Improve the efficiency and effectiveness of cryptographic algorithm and module testing by adopting best practices from the industry;
- Develop test procedures and techniques that provide assurance of cryptographic algorithm correctness and module compliance to FIPS 140 in an automated manner based on machine-readable artifacts or evidence; and
- Identify techniques and procedures that provide continued assurance of operational compliance to FIPS 140 for cryptographic modules throughout their lifecycle.
Scope And Timeline
The scope of this project is broken into multiple phases.
Phase 1
- Identify potential approaches for automating algorithm testing. STATUS: Done.
- Select the best technical approach or approaches to prototype. STATUS: Done.
- Document the technical approach for automated algorithm testing. STATUS: Done. Note: the selected new model for automated cryptographic validation testing shown in the figure below introduces a first-party testing model where module vendors will submit results directly to NIST, without intermediaries. This direct communication and much simplified process will help to achieve the desired goals of modernizing the cryptographic validation programs.
- Target: Q2, 2016. STATUS: Done.
Phase 2
- Develop working prototypes.STATUS: Done.
- Evaluate the prototypes against the principal goals.STATUS: Done.
- Target: Q3, 2016. See the directions at the ACVP GitHub repository for accessing the demo server at https://demo.acvts.nist.gov/acvp/home and its currently supported capabilities. STATUS: Done.
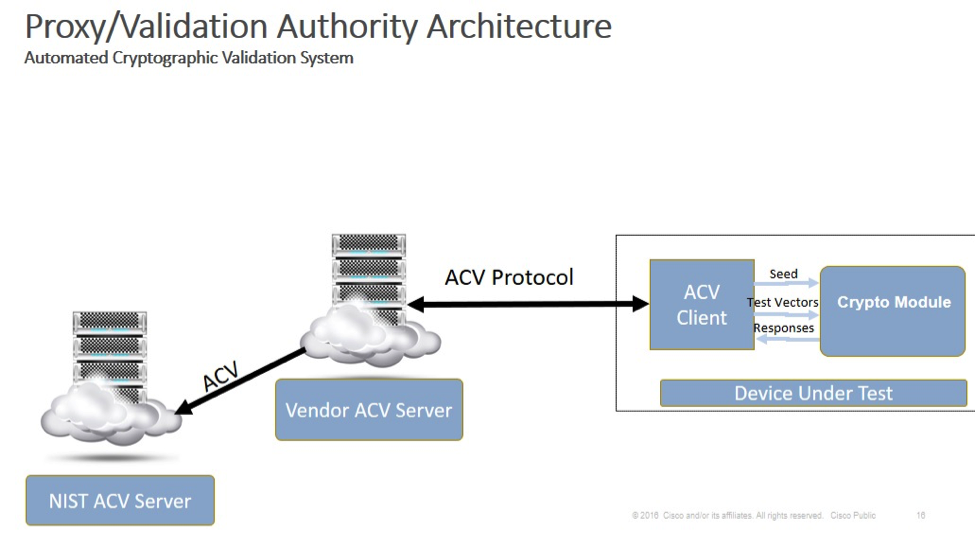
Phase 3
- Publish draft, target Q4, 2016.STATUS: Done. See GitHub ACVP repository for details.
- Review period, adjudication of comments, publish final version, target Q2, 2018. STATUS: In progress.
Phase 4
- Integrate final version into operational CAVP and CMVP programs.STATUS: In progress
- Stand-up a prototype NIST automated algorithm testing service (demo.acvts.nist.gov/acvp) for AES-GCM, Q3, 2016.STATUS: Done.
- Start issuing official algorithm certificates through the automated NIST server (acvts.nist.gov/acvp) based on the ACVP protocol for selected algorithms in May 2017. STATUS: Done.
- Complete a draft accreditation criteria for establishing a new scope in HB 150-17 for automated algorithm validation testing, Q3, 2017. STATUS: Done.
- Roll-out a complete set of CAVP algorithm testing capabilities with automated algorithm testing with acvp.nist.gov based on the ACVP protocol in Q3, 2018. STATUS; In progress.
- Perform a pilot automated cryptographic module validation in Q4, 2018. STATUS: In progress.
- Roll-out an automated cryptographic module test NIST web service and protocol in Q2, 2019. STATUS: In progress.
 An unofficial archive of your favorite United States government website
An unofficial archive of your favorite United States government website




