
special Publication 800-12: An Introduction to Computer Security: The NIST Handbook
Click here for a printable copy for Chapter 19
CHAPTER 19:
Cryptography
Cryptography is a branch of mathematics based on the transformation of data. It provides an important tool for protecting information and is used in many aspects of computer security. For example, cryptography can help provide data confidentiality, integrity, electronic signatures, and advanced user authentication. Although modern cryptography relies upon advanced mathematics, users can reap its benefits without understanding its mathematical underpinnings.
| Cryptography is traditionally associated only with keeping data secret. However, modern cryptography can be used to provide many security services, such as electronic signatures and ensuring that data has not been modified. |
This chapter describes cryptography as a tool for satisfying a wide spectrum of computer security needs and requirements. It describes fundamental aspects of the basic cryptographic technologies and some specific ways cryptography can be applied to improve security. The chapter also explores some of the important issues that should be considered when incorporating cryptography into computer systems.
19.1 Basic Cryptographic Technologies
Cryptography relies upon two basic components: an algorithm (or cryptographic methodology) and a key. In modern cryptographic systems, algorithms are complex mathematical formulae and keys are strings of bits. For two parties to communicate, they must use the same algorithm (or algorithms that are designed to work together). In some cases, they must also use the same key. Many cryptographic keys must be kept secret; sometimes algorithms are also kept secret.
| There are two basic types of cryptography: "secret key" and "public key." |
There are two basic types of cryptography: secret key systems (also called symmetric systems) and public key systems (also called asymmetric systems). Table 19.1 compares some of the distinct features of secret and public key systems. Both types of systems offer advantages and disadvantages. Often, the two are combined to form a hybrid system to exploit the strengths of each type. To determine which type of cryptography best meets its needs, an organization first has to identify its security requirements and operating environment.
| DISTINCT FEATURES | SECRET KEY CRYPTOGRAPHY | PUBLIC KEY CRYPTOGRAPHY |
| NUMBER OF KEYS | Single Key. | Pair of keys. |
| TYPES OF KEYS | Key is secret. | One key is private, and one key is public. |
| PROTECTION OF KEYS | Disclosure and modification. | Disclosure and modification for private keys and modification for public keys. |
| RELATIVE SPEEDS | Faster. | Slower. |
19.1.1 Secret Key Cryptography
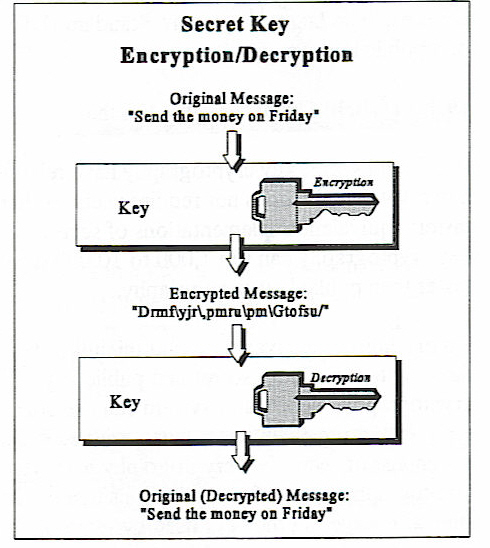
In secret key cryptography, two (or more) parties share the same key, and that key is used to encrypt and decrypt data. As the name implies, secret key cryptography relies on keeping the key secret. If the key is compromised, the security offered by cryptography is severely reduced or eliminated. Secret key cryptography assumes that the parties who share a key rely upon each other not to disclose the key and protect it against modification.
| Secret key cryptography has been in use for centuries. Early forms merely transposed the written characters to hide the message. |
The best known secret key system is the Data Encryption Standard (DES), published by NIST as Federal Information Processing Standard (FIPS) 46-2. Although the adequacy of DES has at times been questioned, these claims remain unsubstantiated, and DES remains strong. It is the most widely accepted, publicly available cryptographic system today. The American National Standards Institute (ANSI) has adopted DES as the basis for encryption, integrity, access control, and key management standards.
The Escrowed Encryption Standard, published as FIPS 185, also makes use of a secret key system. (See the discussion of Key Escrow Encryption in this chapter.)
19.1.2 Public Key Cryptography
| Public key cryptography is a modern invention and requires the use of advanced mathematics. |
Whereas secret key cryptography uses a single key shared by two (or more) parties, public key cryptography uses a pair of keys for each party. One of the keys of the pair is "public" and the other is "private." The public key can be made known to other parties; the private key must be kept confidential and must be known only to its owner. Both keys, however, need to be protected against modification.
Public key cryptography is particularly useful when the parties wishing to communicate cannot rely upon each other or do not share a common key. There are several public key cryptographic systems. One of the first public key systems is RSA, which can provide many different security services. The Digital Signature Standard (DSS), described later in the chapter, is another example of a public key system.
19.1.3 Hybrid Cryptographic Systems
| Secret key systems are often used for bulk data encryption and public key systems for automated key distribution. |
Public and secret key cryptography have relative advantages and disadvantages. Although public key cryptography does not require users to share a common key, secret key cryptography is much faster: equivalent implementations of secret key cryptography can run 1,000 to 10,000 times faster than public key cryptography.
To maximize the advantages and minimize the disadvantages of both secret and public key cryptography, a computer system can use both types in a complementary manner, with each performing different functions. Typically, the speed advantage of secret key cryptography means that it is used for encrypting data. Public key cryptography is used for applications that are less demanding to a computer system's resources, such as encrypting the keys used by secret key cryptography (for distribution) or to sign messages.
19.1.4 Key Escrow
Because cryptography can provide extremely strong encryption, it can thwart the government's efforts to lawfully perform electronic surveillance. For example, if strong cryptography is used to encrypt a phone conversation, a court-authorized wiretap will not be effective. To meet the needs of the government and to provide privacy, the federal government has adopted voluntary key escrow cryptography. This technology allows the use of strong encryption, but also allows the government when legally authorized to obtain decryption keys held by escrow agents. NIST has published the Escrowed Encryption Standard as FIPS 185. Under the federal government's voluntary key escrow initiative, the decryption keys are split into parts and given to separate escrow authorities. Access to one part of the key does not help decrypt the data; both keys must be obtained.
19.2 Uses of Cryptography
 Cryptography
is used to protect data both inside and outside the boundaries
of a computer system. Outside the computer system, cryptography
is sometimes the only way to protect data. While in a computer
system, data is normally protected with logical and physical access
controls (perhaps supplemented by cryptography). However, when in
transit across communications lines or resident on someone else's
computer, data cannot be protected by the originator's134
logical or physical access controls. Cryptography provides a solution
by protecting data even when the data is no longer in the control
of the originator.
Cryptography
is used to protect data both inside and outside the boundaries
of a computer system. Outside the computer system, cryptography
is sometimes the only way to protect data. While in a computer
system, data is normally protected with logical and physical access
controls (perhaps supplemented by cryptography). However, when in
transit across communications lines or resident on someone else's
computer, data cannot be protected by the originator's134
logical or physical access controls. Cryptography provides a solution
by protecting data even when the data is no longer in the control
of the originator.
19.2.1 Data Encryption
One of the best ways to obtain cost-effective data confidentiality is through the use of encryption. Encryption transforms intelligible data, called plaintext135, into an unintelligible form, called ciphertext. This process is reversed through the process of decryption. Once data is encrypted, the ciphertext does not have to be protected against disclosure. However, if ciphertext is modified, it will not decrypt correctly.
Both secret key and public key cryptography can be used for data encryption although not all public key algorithms provide for data encryption.
To use a secret key algorithm, data is encrypted using a key. The same key must be used to decrypt the data.
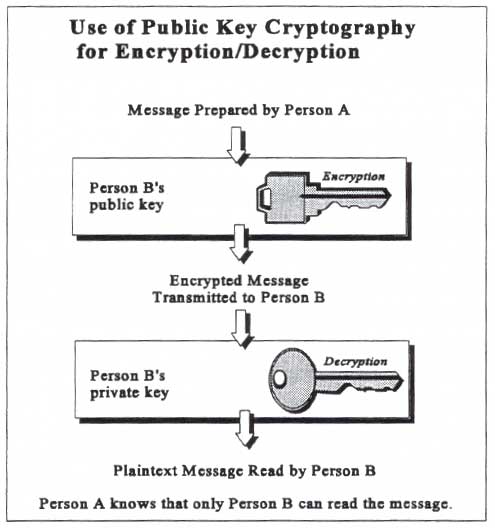 When
public key cryptography is used for encryption, any party may use
any other party's public key to encrypt a message; however, only
the party with the corresponding private key can decrypt, and thus
read, the message.
When
public key cryptography is used for encryption, any party may use
any other party's public key to encrypt a message; however, only
the party with the corresponding private key can decrypt, and thus
read, the message.
Since secret key encryption
is typically much faster, it is normally used for encrypting larger
amounts of data.
19.2.2 Integrity
In computer systems, it is not always possible for humans to scan information to determine if data has been erased, added, or modified. Even if scanning were possible, the individual may have no way of knowing what the correct data should be. For example, "do" may be changed to "do not," or $1,000 may be changed to $10,000. It is therefore desirable to have an automated means of detecting both intentional and unintentional modifications of data.
While error detecting codes have long been used in communications protocols (e.g., parity bits), these are more effective in detecting (and correcting) unintentional modifications. They can be defeated by adversaries. Cryptography can effectively detect both intentional and unintentional modification; however, cryptography does not protect files from being modified. Both secret key and public key cryptography can be used to ensure integrity. Although newer public key methods may offer more flexibility than the older secret key method, secret key integrity verification systems have been successfully integrated into many applications.
When secret key cryptography is used, a message authentication code (MAC) is calculated from and appended to the data. To verify that the data has not been modified at a later time, any party with access to the correct secret key can recalculate the MAC. The new MAC is compared with the original MAC, and if they are identical, the verifier has confidence that the data has not been modified by an unauthorized party. FIPS 113, Computer Data Authentication, specifies a standard technique for calculating a MAC for integrity verification.
Public key cryptography verifies integrity by using of public key signatures and secure hashes. A secure hash algorithm is used to create a message digest. The message digest, called a hash, is a short form of the message that changes if the message is modified. The hash is then signed with a private key. Anyone can recalculate the hash and use the corresponding public key to verify the integrity of the message.136
19.2.3 Electronic Signatures
|
What
Is an Electronic Signature?
An electronic signature is a cryptographic mechanism that performs a similar function to a written signature. It is used to verify the origin and contents of a message. For example, a recipient of data (e.g., an e-mail message) can verify who signed the data and that the data was not modified after being signed. This also means that the originator (e.g., sender of an e-mail message) cannot falsely deny having signed the data. |
Today's computer systems store and process increasing numbers of paper-based documents in electronic form. Having documents in electronic form permits rapid processing and transmission and improves overall efficiency. However, approval of a paper document has traditionally been indicated by a written signature. What is needed, therefore, is the electronic equivalent of a written signature that can be recognized as having the same legal status as a written signature. In addition to the integrity protections, discussed above, cryptography can provide a means of linking a document with a particular person, as is done with a written signature. Electronic signatures can use either secret key or public key cryptography; however, public key methods are generally easier to use.
Cryptographic signatures provide extremely strong proof that a message has not been altered and was signed by a specific key.137 However, there are other mechanisms besides cryptographic-based electronic signatures that perform a similar function. These mechanisms provide some assurance of the origin of a message, some verification of the message's integrity, or both.138
- Examination of the
transmission path of a message. When messages are sent across
a network, such as the Internet, the message source and the physical
path of the message are recorded as a part of the message. These
can be examined electronically or manually to help ascertain the
origin of a message.
- Use of a value-added
network provider. If two or more parties are communicating via
a third party network, the network provider may be able to provide
assurance that messages originate from a given source and have
not been modified.
- Acknowledgment statements. The recipient of an electronic message may confirm
the message's origin and contents by sending back an acknowledgment
statement.
- Use of audit trails. Audit trails can track the sending of messages and their contents for later reference.
Simply taking a digital picture of a written signature does not provide adequate security. Such a digitized written signature could easily be copied from one electronic document to another with no way to determine whether it is legitimate. Electronic signatures, on the other hand, are unique to the message being signed and will not verify if they are copied to another document.
| Systems incorporating message authentication technology have been approved for use by the federal government as a replacement for written signatures on electronic documents. |
19.2.3.1 Secret Key Electronic Signatures
An electronic signature can be implemented using secret key message authentication codes (MACs). For example, if two parties share a secret key, and one party receives data with a MAC that is correctly verified using the shared key, that party may assume that the other party signed the data. This assumes, however, that the two parties trust each other. Thus, through the use of a MAC, in addition to data integrity, a form of electronic signature is obtained. Using additional controls, such as key notarization and key attributes, it is possible to provide an electronic signature even if the two parties do not trust each other.
19.2.3.2 Public Key Electronic Signatures
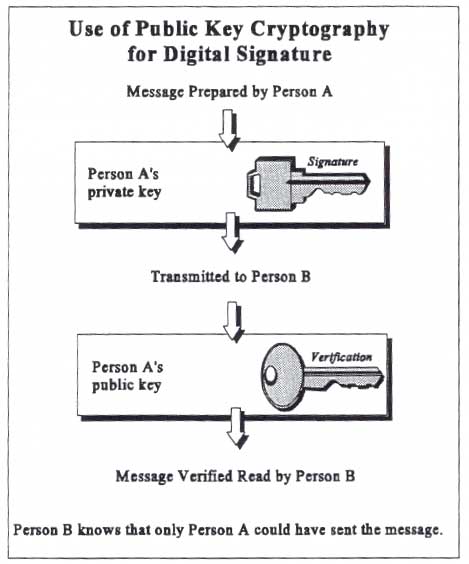 Another
type of electronic signature called a digital signature is
implemented using public key cryptography. Data is electronically
signed by applying the originator's private key to the data. (The
exact mathematical process for doing this is not important for this
discussion.) To increase the speed of the process, the private key
is applied to a shorter form of the data, called a "hash"
or "message digest," rather than to the entire set of
data. The resulting digital signature can be stored or transmitted
along with the data. The signature can be verified by any party
using the public key of the signer. This feature is very useful,
for example, when distributing signed copies of virus-free software.
Any recipient can verify that the program remains virus-free. If
the signature verifies properly, then the verifier has confidence
that the data was not modified after being signed and that the owner
of the public key was the signer.
Another
type of electronic signature called a digital signature is
implemented using public key cryptography. Data is electronically
signed by applying the originator's private key to the data. (The
exact mathematical process for doing this is not important for this
discussion.) To increase the speed of the process, the private key
is applied to a shorter form of the data, called a "hash"
or "message digest," rather than to the entire set of
data. The resulting digital signature can be stored or transmitted
along with the data. The signature can be verified by any party
using the public key of the signer. This feature is very useful,
for example, when distributing signed copies of virus-free software.
Any recipient can verify that the program remains virus-free. If
the signature verifies properly, then the verifier has confidence
that the data was not modified after being signed and that the owner
of the public key was the signer.
NIST has published standards for a digital signature and a secure hash for use by the federal government in FIPS 186, Digital Signature Standard and FIPS 180, Secure Hash Standard.
19.2.4 User Authentication
Cryptography can increase security in user authentication techniques. As discussed in Chapter 16, cryptography is the basis for several advanced authentication methods. Instead of communicating passwords over an open network, authentication can be performed by demonstrating knowledge of a cryptographic key. Using these methods, a one-time password, which is not susceptible to eavesdropping, can be used. User authentication can use either secret or public key cryptography.
19.3 Implementation Issues
This section explores several important issues that should be considered when using (e.g., designing, implementing, integrating) cryptography in a computer system.
19.3.1 Selecting Design and Implementation Standards
| Applicable security standards provide a common level of security and interoperability among users.. |
NIST and other organizations have developed numerous standards for designing, implementing, and using cryptography and for integrating it into automated systems. By using these standards, organizations can reduce costs and protect their investments in technology. Standards provide solutions that have been accepted by a wide community and that have been reviewed by experts in relevant areas. Standards help ensure interopability among different vendors' equipment, thus allowing an organization to select from among various products in order to find cost-effective equipment.
Managers and users of computer systems will have to select among various standards when deciding to use cryptography. Their selection should be based on cost-effectiveness analysis, trends in the standard's acceptance, and interoperability requirements. In addition, each standard should be carefully analyzed to determine if it is applicable to the organization and the desired application. For example, the Data Encryption Standard and the Escrowed Encryption Standard are both applicable to certain applications involving communications of data over commercial modems. Some federal standards are mandatory for federal computer systems, including DES (FIPS 46-2) and the DSS (FIPS 181).
19.3.2 Deciding on Hardware vs. Software Implementations
The trade-offs among security, cost, simplicity, efficiency, and ease of implementation need to be studied by managers acquiring various security products meeting a standard. Cryptography can be implemented in either hardware or software. Each has its related costs and benefits.
In general, software is less expensive and slower than hardware, although for large applications, hardware may be less expensive. In addition, software may be less secure, since it is more easily modified or bypassed than equivalent hardware products. Tamper resistance is usually considered better in hardware.
In many cases, cryptography is implemented in a hardware device (e.g., electronic chip, ROM-protected processor) but is controlled by software. This software requires integrity protection to ensure that the hardware device is provided with correct information (i.e., controls, data) and is not bypassed. Thus, a hybrid solution is generally provided, even when the basic cryptography is implemented in hardware. Effective security requires the correct management of the entire hybrid solution.
19.3.3 Managing Keys
The proper management of cryptographic keys is essential to the effective use of cryptography for security. Ultimately, the security of information protected by cryptography directly depends upon the protection afforded to keys.
All keys need to be protected against modification, and secret keys and private keys need protection against unauthorized disclosure. Key management involves the procedures and protocols, both manual and automated, used throughout the entire life cycle of the keys. This includes the generation, distribution, storage, entry, use, destruction, and archiving of cryptographic keys.
With secret key cryptography, the secret key(s) should be securely distributed (i.e., safeguarded against unauthorized replacement, modification, and disclosure) to the parties wishing to communicate. Depending upon the number and location of users, this task may not be trivial. Automated techniques for generating and distributing cryptographic keys can ease overhead costs of key management, but some resources have to be devoted to this task. FIPS 171, Key Management Using ANSI X9.17, provides key management solutions for a variety of operational environments.
Public key cryptography users also have to satisfy certain key management requirements. For example, since a private-public key pair is associated with (i.e., generated or held by) a specific user, it is necessary to bind the public part of the key pair to the user.139
In a small community of users, public keys and their "owners" can be strongly bound by simply exchanging public keys (e.g., putting them on a CD-ROM or other media). However, conducting electronic business on a larger scale, potentially involving geographically and organizationally distributed users, necessitates a means for obtaining public keys electronically with a high degree of confidence in their integrity and binding to individuals. The support for the binding between a key and its owner is generally referred to as a public key infrastructure.
Users also need to be able enter the community of key holders, generate keys (or have them generated on their behalf), disseminate public keys, revoke keys (in case, for example, of compromise of the private key), and change keys. In addition, it may be necessary to build in time/date stamping and to archive keys for verification of old signatures.
19.3.4 Security of Cryptography Modules
| FIPS 140-1, Security Requirements for Cryptographic Modules, specifies the physical and logical security requirements for cryptographic modules. The standard defines four security levels for cryptographic modules, with each level providing a significant increase in security over the preceding level. The four levels allow for cost-effective solutions that are appropriate for different degrees of data sensitivity and different application environments. The user can select the best module for any given application or system, avoiding the cost of unnecessary security features. |
Cryptography is typically implemented in a module of software, firmware, hardware, or some combination thereof. This module contains the cryptographic algorithm(s), certain control parameters, and temporary storage facilities for the key(s) being used by the algorithm(s). The proper functioning of the cryptography requires the secure design, implementation, and use of the cryptographic module. This includes protecting the module against tampering.
19.3.5 Applying Cryptography to Networks
The use of cryptography within networking applications often requires special considerations. In these applications, the suitability of a cryptographic module may depend on its capability for handling special requirements imposed by locally attached communications equipment or by the network protocols and software.
Encrypted information, MACs, or digital signatures may require transparent communications protocols or equipment to avoid being misinterpreted by the communications equipment or software as control information. It may be necessary to format the encrypted information, MAC, or digital signature to ensure that it does not confuse the communications equipment or software. It is essential that cryptography satisfy the requirements imposed by the communications equipment and does not interfere with the proper and efficient operation of the network.
Data is encrypted on a network using either link or end-to-end encryption. In general, link encryption is performed by service providers, such as a data communications provider. Link encryption encrypts all of the data along a communications path (e.g., a satellite link, telephone circuit, or T1 line). Since link encryption also encrypts routing data, communications nodes need to decrypt the data to continue routing. End-to-end encryption is generally performed by the end-user organization. Although data remains encrypted when being passed through a network, routing information remains visible. It is possible to combine both types of encryption.
19.3.6 Complying with Export Rules
The US government controls the export of cryptographic implementations. The rules governing export can be quite complex, since they consider multiple factors. In addition, cryptography is a rapidly changing field, and rules may change from time to time. Questions concerning the export of a particular implementation should be addressed to appropriate legal counsel.
19.4 Interdependencies
There are many interdependencies among cryptography and other security controls highlighted in this handbook. Cryptography both depends on other security safeguards and assists in providing them.
Physical Security. Physical protection of a cryptographic module is required to prevent -- or at least detect --- physical replacement or modification of the cryptographic system and the keys within it. In many environments (e.g., open offices, portable computers), the cryptographic module itself has to provide the desired levels of physical security. In other environments (e.g., closed communications facilities, steel-encased Cash-Issuing Terminals), a cryptographic module may be safely employed within a secured facility.
User Authentication. Cryptography can be used both to protect passwords that are stored in computer systems and to protect passwords that are communicated between computers. Furthermore, cryptographic-based authentication techniques may be used in conjunction with, or in place of, password-based techniques to provide stronger authentication of users.
Logical Access Control. In many cases, cryptographic software may be embedded within a host system, and it may not be feasible to provide extensive physical protection to the host system. In these cases, logical access control may provide a means of isolating the cryptographic software from other parts of the host system and for protecting the cryptographic software from tampering and the keys from replacement or disclosure. The use of such controls should provide the equivalent of physical protection.
Audit Trails. Cryptography may play a useful role in audit trails. For example, audit records may need to be signed. Cryptography may also be needed to protect audit records stored on computer systems from disclosure or modification. Audit trails are also used to help support electronic signatures.
Assurance. Assurance that a cryptographic module is properly and securely implemented is essential to the effective use of cryptography. NIST maintains validation programs for several of its standards for cryptography. Vendors can have their products validated for conformance to the standard through a rigorous set of tests. Such testing provides increased assurance that a module meets stated standards, and system designers, integrators, and users can have greater confidence that validated products conform to accepted standards.
| NIST maintains validation programs for several of its cryptographic standards. |
A cryptographic system should be monitored and periodically audited to ensure that it is satisfying its security objectives. All parameters associated with correct operation of the cryptographic system should be reviewed, and operation of the system itself should be periodically tested and the results audited. Certain information, such as secret keys or private keys in public key systems, should not be subject to audit. However, nonsecret or nonprivate keys could be used in a simulated audit procedure.
19.5 Cost Considerations
Using cryptography to protect information has both direct and indirect costs. Cost is determined in part by product availability; a wide variety of products exist for implementing cryptography in integrated circuits, add-on boards or adapters, and stand-alone units.
19.5.1 Direct Costs
The direct costs of cryptography include:
- Acquiring or implementing
the cryptographic module and integrating it into the computer system.
The medium (i.e., hardware, software, firmware, or combination)
and various other issues such as level of security, logical and
physical configuration, and special processing requirements will
have an impact on cost.
- Managing the cryptography and, in particular, managing the cryptographic keys, which includes key generation, distribution, archiving, and disposition, as well as security measures to protect the keys, as appropriate.
19.5.2 Indirect Costs
The indirect costs of cryptography include:
- A decrease in system
or network performance, resulting from the additional overhead of
applying cryptographic protection to stored or communicated data.
- Changes in the way users interact with the system, resulting from more stringent security enforcement. However, cryptography can be made nearly transparent to the users so that the impact is minimal.
References
Alexander, M., ed. "Protecting Data With Secret Codes," Infosecurity News. 4(6), 1993. pp. 72-78.
American Bankers Association. American National Standard for Financial Institution Key Management (Wholesale). ANSI X9.17-1985. Washington, DC., 1985.
Denning, P., and D. Denning, "The Clipper and Capstone Encryption Systems." American Scientist. 81(4), 1993. pp. 319-323.
Diffie, W., and M. Hellman. "New Directions in Cryptography." IEEE Transactions on Information Theory. Vol. IT-22, No. 6, November 1976. pp. 644-654.
Duncan, R. "Encryption ABCs." Infosecurity News. 5(2), 1994. pp. 36-41.
International Organization for Standardization. Information Processing Systems - Open Systems Interconnection Reference Model - Part 2: Security Architecture. ISO 7498/2. 1988.
Meyer, C.H., and S. M. Matyas. Cryptography: A New Dimension in Computer Data Security. New York, NY: John Wiley & Sons, 1982.
Nechvatal, James. Public-Key Cryptography. Special Publication 800-2. Gaithersburg, MD: National Institute of Standards and Technology, April 1991.
National Bureau of Standards. Computer Data Authentication. Federal Information Processing Standard Publication 113. May 30, 1985.
National Institute of Standards and Technology. "Advanced Authentication Technology." Computer Systems Laboratory Bulletin. November 1991.
National Institute of Standards and Technology. Data Encryption Standard. Federal Information Processing Standard Publication 46-2. December 30, 1993.
National Institute of Standards and Technology. "Digital Signature Standard." Computer Systems Laboratory Bulletin. January 1993.
National Institute of Standards and Technology. Digital Signature Standard. Federal Information Processing Standard Publication 186. May 1994.
National Institute of Standards and Technology. Escrowed Encryption Standard. Federal Information Processing Standard Publication 185. 1994.
National Institute of Standards and Technology. Key Management Using ANSI X9.17. Federal Information Processing Standard Publication 171. April 27, 1992.
National Institute of Standards and Technology. Secure Hash Standard. Federal Information Processing Standard Publication 180. May 11, 1993.
National Institute of Standards and Technology. Security Requirements for Cryptographic Modules. Federal Information Processing Standard Publication 140-1. January 11, 1994.
Rivest, R., A. Shamir, and L. Adleman. "A Method for Obtaining Digital Signatures and Public-Key Cryptosystems." Communications of the ACM., Vol. 21, No. 2, 1978. pp. 120-126.
Saltman, Roy G., ed. Good Security Practices for Electronic Commerce, Including Electronic Data Interchange. Special Publication 800-9. Gaithersburg, MD: National Institute of Standards and Technology. December 1993.
Schneier, B. "A Taxonomy of Encryption Algorithms." Computer Security Journal. 9(1), 1993. pp. 39-60.
Schneier, B. "Four Crypto Standards." Infosecurity News. 4(2), 1993. pp.38-39.
Schneier, B. Applied Cryptography: Protocols, Algorithms, and Source Code in C. New York, NY: John Wiley & Sons, Inc., 1994.
U.S. Congress, Office of Technology Assessment. "Security Safeguards and Practices." Defending Secrets, Sharing Data: New Locks and Keys for Electronic Information. Washington, DC: 1987, pp. 54-72.
|
|
Footnotes:
134.
The originator does not have to be the original creator of the data.
It can also be a guardian or custodian of the data.
135. Plaintext can be intelligible to a human
(e.g., a novel) or to a machine (e.g., executable code).
136. Sometimes a secure hash is used for integrity
verification. However, this can be defeated if the hash is not stored
in a secure location, since it may be possible for someone to change
the message and then replace the old hash with a new one based on
the modified message.
137. Electronic signatures rely on the secrecy
of the keys and the link or binding between the owner of the key
and the key itself. If a key is compromised (by theft, coercion,
or trickery), then the electronic originator of a message may not
be the same as the owner of the key. Although the binding of cryptographic
keys to actual people is a significant problem, it does not necessarily
make electronic signatures less secure than written signatures.
Trickery and coercion are problems for written signatures as well.
In addition, written signatures are easily forged.
138. The strength of these mechanisms relative
to electronic signatures varies depending on the specific implementation;
however, in general, electronic signatures are stronger and more
flexible. These mechanisms may be used in conjunction with electronic
signatures or separately, depending upon the system's specific needs
and limitations.
139. In some cases, the key may be bound to a
position or an organization, rather than to an individual user.