Validation Process Flow
Process from Vendor to Validation
The figure below illustrates the interactions that happen between Vendor, CST Lab, and CMVP. The MIP list indicates one of fives steps in the process for each validation. Each step is addressed in the figure and the legend below. For more information, please refer to Section 4 of the Management Manual. 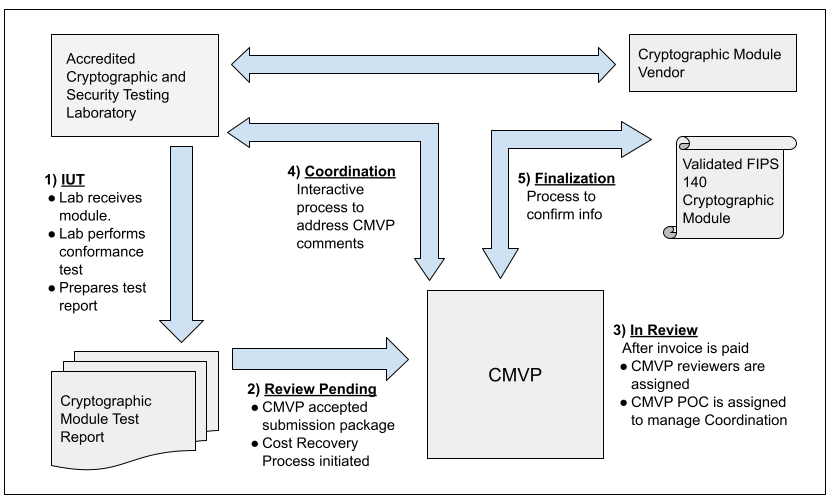
The steps for the cryptographic module validation life cycle include:
Step 1 - IUT.
The vendor submits the cryptographic module for testing to an accredited CST laboratory under a contractual agreement. Cryptographic module validation testing is performed using the Derived Test Requirements (DTR). If the CST laboratory has any questions or requires clarification of any requirement in regards to the particular cryptographic module, the laboratory can submit Requests for Guidance (RFG) to NIST and CCCS as described in the Management Manual Section 2.4 Request for Guidance from CMVP.
Step 2 - Review Pending.
Once all the testing requirements have been completed, a validation submission is prepared. The Cost Recovery fees are addressed prior to or with the submission.
Step 3 - In Review.
The validation submission is sent to CMVP. After the payment has been processed, two reviewers are assigned to perform the initial review of the documents. One of the reviewers is identified as the point of contact (POC) for CMVP to interact with the CST laboratory to address comments.
Step 4 - Coordination.
The coordination process will continue until all comments and/or questions have been satisfactorily addressed.
Step 5 - Finalization.
Once the cryptographic module has been validated, and the associated vendor information has been confirmed by the laboratory, the validation information is posted to the CMVP Validation List at the CMVP website: Search.
 An unofficial archive of your favorite United States government website
An unofficial archive of your favorite United States government website


