FIPS 140-3 Standards
Documentation and Governance for the FIPS 140-3 Cryptographic Module Validation Program
Federal Information Processing Standards Publication (FIPS) 140-3 became effective September 22, 2019, permitting CMVP to begin accepting validation submissions under the new scheme beginning September 2020. The FIPS 140-3 standard introduces some significant changes in the management over the previous standard. Rather than encompassing the module requirements directly, FIPS 140-3 references International Organization for Standardization/International Electrotechnical Commission (ISO/IEC) 19790. The testing for these requirements will be in accordance with ISO/IEC 24759.
FIPS 140-3 Top Level Documents
| Document |
Title |
Status |
CMVP Control |
ISO/IEC Control |
| FIPS 140-3 |
Security requirements for cryptographic equipment |
Published Mar 2019 |
Yes |
No |
| ISO/IEC 19790 |
Security requirements for cryptographic modules |
Published Aug 2015 |
No |
Yes |
| ISO/IEC 24759 |
Test requirements for cryptographic modules |
Published Mar 2017 |
No |
Yes |
| Management Manual |
FIPS 140-3 Cryptographic Module Validation Program Management Manual |
Working Draft Sep 2020 |
Yes |
No |
| Implementation Guidance |
Implementation Guidance for FIPS 140-3 and the Cryptographic Module Validation Program |
Published Nov 2021
|
Yes |
No |
ISO/IEC 19790 and ISO/IEC 24759 standards, each individual must have one!
Unlike the FIPS 140-2 Standard which included the requirements for cryptographic modules, the FIPS 140-3 references ISO/IEC 19790:2012 and ISO/IEC 24759:2017 which can be purchased through the International Organization for Standardization Store. If you already have the ISO/IEC 19790:2012, make sure it contains the 2015 update. There is much confusion as ISO/IEC normally posts a Technical Corrigendum listing only the changes to the standard. However, ISO/IEC has withdrawn the Technical Corrigendum, and has folded the updates into the ISO/IEC 19790:2012 now available. The update is internally marked as ISO/IEC 19790:2012/Cor.1:2015(E).
ISO publications can only be bought for your personal individual use and cannot be transferred to another user. If you wish to purchase (an) ISO publication(s) for multiple users (for example, for your colleagues or post on your company’s intranet) or want to obtain broader rights beyond your personal use, please contact ISO or your ISO Member to explore your options.
NIST intends to work with the appropriate parties to help ensure that the ISO/IEC standard will be made reasonably available to researchers, academics and small organizations. To support this effort, NIST is currently making available a limited number of copies of ISO/IEC 19790:2012 and ISO/IEC 24759:2017. To request a copy of each document, complete the Contact Information form and then email a copy of your signed End User License Agreement to cmvpiso@nist.gov.
Back to Top
SP 800-140 Documents
| Special Publication
|
Title |
Status |
ISO/IEC 19790 |
ISO/IEC 24759 |
| SP 800-140 |
FIPS 140-3 Derived Test Requirements (DTR) |
Published Mar 2020 |
— |
§6.1 –§6.12 |
| SP 800-140A |
CMVP Documentation Requirements |
Published Mar 2020 |
Annex A |
§6.13 |
| SP 800-140B |
CMVP Security Policy Requirements |
Published Mar 2020 |
Annex B |
§6.14 |
| SP 800-140C |
CMVP Approved Security Functions |
Published Mar 2020 |
Annex C |
§6.15 |
| SP 800-140C Rev. 1 (Draft) |
CMVP Approved Security Functions |
Published Aug 2021 |
Annex C |
§6.15 |
| SP 800-140D |
CMVP Approved Sensitive Security Parameter Generation and Establishment Methods |
Published Mar 2020 |
Annex D |
§6.16 |
| SP 800-140D Rev. 1 (Draft) |
CMVP Approved Sensitive Security Parameter Generation and Establishment Methods |
Published Aug 2021 |
Annex D |
§6.16 |
| SP 800-140E |
CMVP Approved Authentication Mechanisms |
Published Mar 2020 |
Annex E |
§6.17 |
| SP 800-140F |
CMVP Approved Non-Invasive Attack Mitigation Test Metrics |
Published Mar 2020 |
Annex F |
§6.18 |
| SP 800-140F Rev. 1 (Draft) |
CMVP Approved Non-Invasive Attack Mitigation Test Metrics |
Published Aug 2021 |
Annex F |
§6.18 |
Back to Top
Document Process Flow
The use of the ISO documents require several procedural changes in the management and execution of the validation process from the existing FIPS 140-2 process currently in effect. The figure below demonstrates the flow of the requirements for the FIPS 140-3 process.
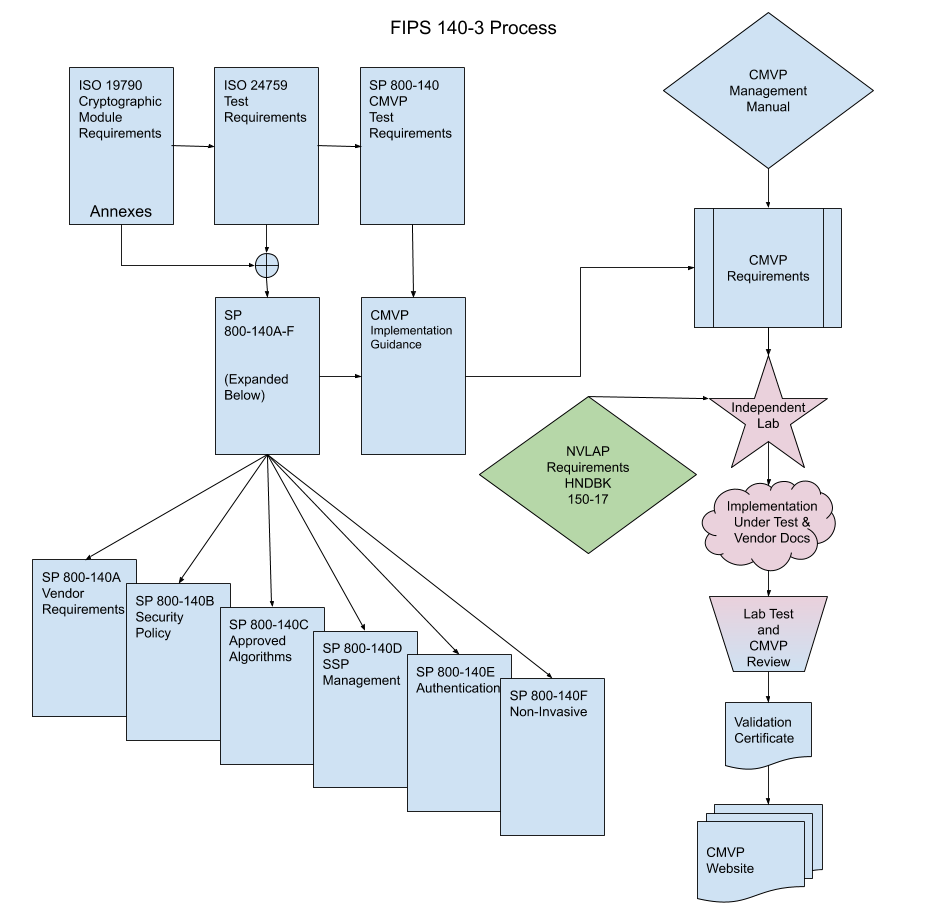
The ISO/IEC 19790 specifies the cryptographic module requirements, along with the associated guidance issued through the Annexes. ISO/IEC 24759 extracts the requirements of ISO/IEC 19790 and associates vendor information and lab procedures to assure the requirements are met.
The CMVP manages the variances allowed in the ISO/IEC 19790 and ISO/IEC 24759 through the SP 800-140x documents. Specifically, the SP 800-140 provides additional evidence and testing that is necessary to meet CMVP cryptographic module requirement evidence, while also providing to ISO/IEC recommended adjustments to the existing standard when next reviewed. The remaining SP 800-140A through SP 800-140F provide additional requirements for vendor evidence, security policy, approved encryption and key management, authentication and non-invasive physical security requirements.
Clarification or interpretation of the requirements and assurance measures are included in the Implementation Guidance, which are often technology specific. A standalone document, the FIPS 140-3 CMVP management manual, addresses the programmatic procedures and requirements of the process. In addition, NVLAP Handbook 150-17 identifies CMVP specific NVLAP requirements which includes requirements in quality systems, personnel, environmental conditions, test and calibration methods, equipment, test quality assurance, and reporting results control.
Independent test labs holding appropriate NVLAP accreditation, manage and perform the testing process. The labs create a submission package with the results of the assessment which CMVP reviews and coordinates any resulting comments with the lab. Upon satisfactory agreement, a validation is issued and added to the database of validated modules hosted on the CMVP website.
Back to Top
Abstracts
Federal Information Processing Standards FIPS 140-3 identifies the Cryptographic Module Validation Program (CMVP), a joint effort of the US and Canadian governments, as the validation authority for implementing a program utilizing the ISO/IEC 19790:2012 requirements standard and ISO/IEC 24759:2017 derived test methods. The standard also established the CMVP technical requirements to be contained in NIST Special Publications: SP 800-140, SP 800-140A, SP 800-140B, SP 800-140C, SP 800-140D, SP 800-140E,and SP 800-140F. These security requirements must be satisfied by a cryptographic module utilized within a security system protecting sensitive but unclassified information (hereafter referred to as sensitive information). This standard will supersede FIPS 140-2, Security Requirements for Cryptographic Modules, in its entirety.
ISO/IEC 19790:2012 specifies the security requirements for a cryptographic module utilized within a security system protecting sensitive information in computer and telecommunication systems. This International Standard defines four security levels for cryptographic modules to provide for a wide spectrum of data sensitivity (e.g. low value administrative data, million dollar funds transfers, life protecting data, personal identity information, and sensitive information used by government) and a diversity of application environments (e.g. a guarded facility, an office, removable media, and a completely unprotected location). This International Standard specifies four security levels for each of 11 requirement areas with each security level increasing security over the preceding level.
ISO/IEC 24759:2017 specifies the methods to be used by testing laboratories to test whether the cryptographic module conforms to the requirements specified in ISO/IEC 19790:2012. The methods are developed to provide a high degree of objectivity during the testing process and to ensure consistency across the testing laboratories. This document also specifies the requirements for information that vendors provide to testing laboratories as supporting evidence to demonstrate their cryptographic modules’ conformity to the requirements specified in ISO/IEC 19790:2012.
NIST Special Publication (SP) 800-140 specifies the Derived Test Requirements (DTR) for Federal Information Processing Standard (FIPS) 140-3. SP 800-140 modifies the test (TE) and vendor (VE) evidence requirements of ISO/IEC 24759. As a validation authority, the Cryptographic Module Validation Program (CMVP) may modify, add or delete TEs and/or VEs as specified under paragraph 5.2 of ISO/IEC 24759. This NIST Special Publication should be used in conjunction with ISO/IEC 24759 as it modifies only those requirements identified in this document.
NIST Special Publication (SP) 800-140A modifies the vendor documentation requirements of ISO/IEC 19790 Annex A. As a validation authority, the Cryptographic Module Validation Program (CMVP) may modify, add or delete Vendor Evidence (VE) and/or Test Evidence (TE) as specified under paragraph 5.2 of the ISO/IEC 19790. This document should be used in conjunction with ISO/IEC 19790 Annex A and ISO/IEC 24759 paragraph 6.13 as it modifies only those requirements identified in this document.
NIST Special Publication (SP) 800-140B is to be used in conjunction with ISO/IEC 19790 Annex B and ISO/IEC 24759 6.14. The special publication modifies only those requirements identified in this document. SP 800-140B also specifies the content of the tabular and graphical information required in ISO/IEC 19790 Annex B. As a validation authority, the Cryptographic Module Validation Program (CMVP) may modify, add or delete Vendor Evidence (VE) and/or Test Evidence (TE) specified under paragraph 6.14 of the ISO/IEC 24759 and as specified in ISO/IEC 19790 paragraph B.1.
NIST Special Publication (SP) 800-140C replaces the approved security functions of ISO/IEC 19790 Annex C. As a validation authority, the Cryptographic Module Validation Program (CMVP) may supersede this Annex in its entirety. This document supersedes ISO/IEC 19790 Annex C and ISO/IEC 24759 paragraph 6.15.
NIST Special Publication (SP) 800-140D replaces the approved sensitive parameter generation and establishment methods requirements of ISO/IEC 19790 Annex D. As a validation authority, the Cryptographic Module Validation Program (CMVP) may supersede this Annex in its entirety. This document supersedes ISO/IEC 19790 Annex D and ISO/IEC 24759 paragraph 6.16.
NIST Special Publication (SP) 800-140E replaces the approved authentication mechanism requirements of ISO/IEC 19790 Annex E. As a validation authority, the Cryptographic Module Validation Program (CMVP) may supersede this Annex in its entirety with its own list of approved authentication mechanisms. This document supersedes ISO/IEC 19790 Annex E and ISO/IEC 24759 paragraph 6.17.
NIST Special Publication (SP) 800-140F replaces the approved non-invasive attack mitigation test metric requirements of ISO/IEC 19790 Annex F. As a validation authority, the Cryptographic Module Validation Program (CMVP) may supersede this Annex in its entirety. This document supersedes ISO/IEC 19790 Annex F and ISO/IEC 24759 paragraph 6.18.
Back to Top
 An unofficial archive of your favorite United States government website
An unofficial archive of your favorite United States government website


